Five years ago, cases involving ransomware attacks were viewed as one-off occurrences; that is, a hospital would be attacked, the incident would go around, and people would go on with their lives.
Ransomware attacks today become more pervasive as they target organizations across sectors and regions. Not only has the number of attacks changed, but the way the structure for ransomware attacks has also been altered. That is, therefore, a distinct stage within Ransomware Evolution, as it has progressed from being isolated crimes to a pervasive threat world over.
How Ransomware Has Evolved?
Ransomware, as a product, was quite challenging to implement a decade or more ago. Sufficient knowledge about systems, networking, as well as software development, was required.
They needed to find vulnerabilities and then gain access manually, and then write malware that worked reliably. And even so, many attacks failed. In the early stages, the use of encryption tended to be inadequately implemented, which made organizations capable of regaining data without any payment in exchange for a decrypt key or service
That paradigm began to shift when attackers realized that they did not have to do it all for themselves. Rather, instead of a lone attacker creating and delivering an attack, a lone group could create the foundation of the malware and allow others to use it in return for a piece of the profits. A tool, used by dozens of attackers, would mean dozens of attacks happening at the same time.
And that marked the transition at which point ransomware went from being an underground technical phenomenon to an organized, profit-driven process. The Ransomware Evolution phase that follows represents the future attacks that we shall encounter.
Why Launching Ransomware Is Easier Today?
Today, launching a ransomware attack no longer requires advanced technical skill. The entire ecosystem is available for purchase. Malware kits, step-by-step instructions, customer support–style forums, and even pre-compromised network access are sold openly in criminal marketplaces.
An attacker can simply pay for the tools, follow a guide, and wait for the payout. The barrier to entry has dropped dramatically. This is often described as commoditization, similar to how complex products once required deep expertise to build but can now be bought off the shelf. Ransomware has followed the same path, making large-scale exploitation easier than ever.
Understanding Ransomware as a Service
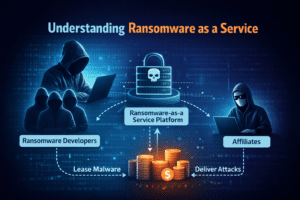
Ransomware-as-a-service has quite a technical name, but the process is quite simple. A group of criminals creates the malware and operates it as a service for the affiliates. The affiliate delivers the ransomware to the business and then shares the ransom with the creators.
In reality, it is like a rental service. The malware coders work on upgrading the malware and on avoiding detection. The affiliates work on infiltrating and launching an attack. The division of labor enables both parties to work in a more efficient and large-scale manner.
What this means is that there is an explosion of cyber-attacks not because there are many highly skilled hackers, but because specialist-quality hacking tools are available to many criminals. In many instances, all that it takes is just one stolen password, one phishing message, and time.
The Role of Initial Access Brokers
One of the most important players in this ecosystem is the Initial Access Broker. Their sole job is to gain entry into corporate networks. They do not deploy ransomware or steal data themselves. Instead, they quietly establish access and then sell it to others.
Effectively, they are selling keys to compromised networks. In this case, one criminal possesses the required access, other buys that access, with a third conducting the ransomware attack. The end result has been that ransomware has basically become an assembly-line process thanks to specialization by all the involved actors.
The Rise of Double and Triple Extortion
Early ransomware attacks followed a simple pattern. Files were encrypted, a ransom was demanded, and organizations with good backups could recover quickly and avoid paying.
Attackers adapted. They began stealing data before encrypting systems. Now, even if an organization restores its systems within hours, it still faces the threat of sensitive customer or employee data being leaked publicly. This tactic, known as double extortion, significantly raises the pressure to pay.
Some groups have gone further, introducing triple extortion. Beyond threatening the victim organization, attackers target customers, partners, or suppliers, warning that their data will also be exposed. This expands the impact beyond a single company and increases reputational, legal, and regulatory risk.
The Geopolitical Dimension
Ransomware has gone beyond being a concern for law enforcement. The situation has been complicated by geopolitics. In some areas, the government does not exactly condone the presence of ransomware gangs operating in their territory. The gangs, on the other hand, neither receive any outright support nor find themselves safeguarded as long as they refrain from holding local businesses for ransom.
And there are definite strategic reasons for this tolerance. Attacks may target alien aggressors, profit could loop through the community, and the damage level is not considered sufficient to constitute a full-scale war. Ransomware is a gray area where a level of damage is possible without necessarily triggering a war response.
Why Ransomware Is a Global Threat?

When you combine easily accessible tools, highly organized criminal networks, specialized roles, and state-level tolerance, ransomware becomes extremely difficult to contain. What we see now are sustained global ransomware attacks, coordinated across borders and time zones, without a single point of control or failure.
This is today’s reality. To understand how ransomware reached this point is to understand how businesses can even think realistically about prevention, resilience, and response. Ransomware is no longer a sporadic incident; it is a permanent feature of the modern digital risk landscape.
Comments
Join the discussion. We’d love to hear your thoughts.