Introduction to DMARC
Email is the lifeblood of modern business communication — but it’s also a major vector for cyberattacks. From phishing scams to brand impersonation, your domain could be exploited without you even knowing. That’s where DMARC (Domain-based Message Authentication, Reporting & Conformance) comes in. It’s more than just a buzzword — it’s a critical defense layer that ensures only trusted sources can send emails using your domain name.
This comprehensive guide will walk you through everything you need to know about DMARC: what it is, how it works, how to implement it, and — most importantly — what happens if you don’t.
What Is DMARC?
It is an email authentication protocol that helps prevent domain spoofing by working with two existing mechanisms — SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). It adds policy enforcement and reporting, allowing domain owners to instruct email receivers how to handle messages that fail authentication, and to receive detailed reports on email activity using their domain.
Why Is DMARC So Important?
- Stops Email Spoofing: It prevents cybercriminals from sending emails that look like they come from your domain.
- Protects Your Brand: Customers are less likely to fall for phishing attacks impersonating your brand.
- Boosts Email Deliverability: Authenticated emails are more trusted by ISPs and less likely to land in the spam folder.
- Provides Full Visibility: You gain insight into who’s using your domain and how — both legitimately and fraudulently.
- Helps Compliance: It can aid with compliance standards like GDPR, HIPAA, and ISO by securing communications.
What Happens If You Don’t Implement DMARC?
Without DMARC in place, your domain is left open to misuse — and the consequences can be serious:
| Risk | Impact |
|---|---|
| Domain Spoofing | Attackers can send emails pretending to be from your domain. |
| Phishing Attacks | Fraudulent emails targeting your customers/employees can steal data. |
| Brand Reputation Loss | Trust erosion from customers who receive malicious emails “from you”. |
| Increased Spam Labeling | Your legitimate emails may be flagged or blocked by recipient servers. |
| No Reporting Insight | You won’t know if or how your domain is being abused. |
| Legal & Compliance Risks | Data leaks via phishing may result in lawsuits or penalties. |
Even large companies like Facebook, PayPal, and Amazon have fallen victim to phishing campaigns using spoofed domains — and they all now actively use DMARC to mitigate these threats.
DMARC Record Breakdown
A DMARC record is a special TXT record you add to your DNS. Here’s an example:
makefileCopyEdit
Value: v=DMARC1; p=reject; rua=mailto:reports@yourdomain.com; pct=100
Let’s break that down:
v=DMARC1: The protocol version.p=reject: The policy to apply (none,quarantine, orreject) if messages fail authentication.rua=: Where aggregate reports should be sent.ruf=: (Optional) Where forensic reports should be sent.pct=100: The percentage of messages the policy should apply to.
How DMARC Works
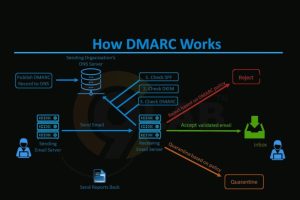
When a receiving mail server gets your email, here’s what happens:
- SPF and DKIM Authentication Check – The server validates that the sender’s IP is authorized and that the email hasn’t been altered.
- Alignment Check – The domain in the “From” address must align with the domains in SPF/DKIM.
- Policy Enforcement – Based on your DMARC policy (
none,quarantine, orreject), the email is delivered, flagged, or blocked. - Reporting – Reports are sent to the
ruaandrufaddresses, detailing what passed or failed.
Step-by-Step: How to Implement DMARC
1. Set Up SPF and DKIM
- Make sure all mail-sending services are included in your SPF record.
- Enable DKIM for cryptographic validation.
2. Publish a Monitoring DMARC Record
- Start with
p=noneto collect data without affecting mail flow.
3. Monitor Reports
- Analyze reports to spot unauthorized sources or misconfigured senders.
4. Adjust Your Policy
- Move to
quarantineto start flagging unverified emails. - Finally shift to
rejectto block them altogether.
5. Maintain and Fine-Tune
- Add new sending services to SPF/DKIM.
- Monitor continuously — DMARC is not a “set and forget” protocol.
Recommended Tools
Here are some tools that can make life easier when implementing DMARC:
| Tool | Use Case |
|---|---|
| MXToolbox | DMARC lookup, blacklist monitoring, SPF/DKIM tests |
| EasyDMARC | Setup, reports, dashboards, alerts |
| Business Risk Score (BRS) | DMARC, SPF/DKIM, SSL, Page load time, DNS WHOIS Records |
| Dmarcian | Visualization of DMARC reports, guided setup |
| PowerDMARC | Enterprise-grade analytics and domain security |
| Google Postmaster Tools | Email reputation and authentication insights |
Best Practices & Tips
- Use a Subdomain for Reports: Avoid spamming your core inbox by setting up a dedicated mailbox.
- Don’t Skip Alignment: Ensure your SPF and DKIM records are aligned to the same domain used in the “From” address.
- Monitor Before Enforcing: Jumping to
p=rejecttoo quickly can block legitimate mail. - Keep a Change Log: Document updates to SPF/DKIM to avoid debugging chaos later.
Check Your DMARC Status & More with C9Lab’s BRS
C9Lab’s Business Risk Score (BRS) is a one-stop solution to check your DMARC, SPF, and DKIM status—ensuring your domain is protected against spoofing and phishing.
But it doesn’t stop there.
BRS also evaluates:
- Email Security: Authentication, phishing risk, blacklists
- Website Performance: Speed, mobile-friendliness, SEO vitals
- External Threats: SSL, HTTPS, headers, vulnerabilities
- Domain Safety: WHOIS, DNS, hijack risk
- Dark Web Exposure: Data leaks, reputation risks
💡 Get a clear risk score + actionable insights.
👉 Check your domain now
For full details on BRS features, read our in-depth guide here.
Conclusion
DMARC is no longer optional. With phishing attacks growing more sophisticated, failing to secure your domain can cost you money, trust, and legal trouble. By implementing and gradually tightening your policy, you not only protect your domain — you protect your people, your brand, and your future.
So don’t wait until a phishing scam hits your inbox with your company’s name on it. Take control with DMARC today.
FAQs
What happens if I don’t set up DMARC?
Without DMARC, your domain is vulnerable to email spoofing and phishing attacks. Malicious actors can impersonate your domain to send fraudulent emails, potentially damaging your brand’s reputation and compromising recipient security. Implementing DMARC helps mitigate these risks by providing a mechanism to authenticate legitimate emails and reject unauthorized ones.
How can I check if my DMARC record is set up correctly?
Use online tools like MXToolbox or DMARC Analyzer to check your domain’s DMARC record. These tools can verify the presence and correctness of your DMARC record and provide insights into any issues that need to be addressed.
How to check my DMARC status?
Business Risk Score (BRS) by C9Lab can also help assess your DMARC status. The BRS tool provides an in-depth analysis of your email security setup, including DMARC, SPF, and DKIM configuration, allowing you to understand your domain’s risk exposure and improve your email security posture. The BRS will give you actionable insights into how to strengthen your email security and protect your domain.
Is DMARC related to SPF and DKIM?
Yes, DMARC is closely related to both SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). Here’s how they work together:
SPF: SPF allows the domain owner to specify which mail servers are authorized to send emails on behalf of their domain.
DKIM: DKIM involves adding a digital signature to emails to verify their authenticity and ensure they haven’t been tampered with in transit.
DMARC: DMARC builds on SPF and DKIM by providing a mechanism for email receivers to check the alignment between the “From” address and the domains authenticated by SPF and DKIM. It helps enforce policies and take action (e.g., quarantine or reject) on emails that fail authentication.
To Stay updated with the latest trends and new in cybersecurity sphere follow our newsletter- Cyber Briefs