Welcome to the second chapter of my Mobile Penetration Testing Series, where we’re turning you into a mobile app security pro! In Part 1, you learned what Android pentesting is, how Android and iOS differ, the structure of .apk and .ipa files, why testing them matters, and the basics of static and dynamic analysis. Now, we’re rolling up our sleeves to set up your testing lab, explore common vulnerabilities, and try simple testing techniques to uncover app weaknesses. Think of yourself as a cyber detective, ready to catch apps misbehaving. Let’s dive into the action!
Disclaimer: This content is for educational purposes only. Always test with explicit permission. Unauthorized testing is illegal and can lead to serious consequences.
Setting Up Your Testing Lab
To start hunting vulnerabilities, you need a lab to test apps safely and ethically. Here’s a beginner-friendly setup to get you going.
Your Equipment
- Computer: Any modern laptop (Windows, macOS, Linux). Kali Linux is a great choice, preloaded with security tools for pentesting.
- Mobile Targets:
- Android: Use Android Studio’s emulator or Genymotion for a faster, smoother experience. A physical Android device works too (no rooting needed yet).
- iOS: Xcode’s simulator on a Mac is the easiest option. Jailbroken iPhones are riskier due to warranty issues, so stick to simulators for now.
- Network: Use an isolated network or VPN to keep your tests secure and private.
Your Tools
Here’s a beginner’s toolkit, mostly free and ready to uncover app secrets:
- Burp Suite Community Edition: Intercepts HTTP/HTTPS traffic to analyze app communication. Free at portswigger.net.
- ADB (Android Debug Bridge): A command-line tool for interacting with Android devices or emulators. Included with Android Studio.
- MobSF (Mobile Security Framework): An open-source tool for static and dynamic analysis. Download from GitHub.
- Frida: A dynamic analysis tool for hooking into app processes, ideal for testing authentication bypasses.
- APKTool: Decompiles Android APKs to inspect their code and configuration.
- Genymotion: A fast Android emulator, free for personal use at genymotion.com.
Setup Steps
- Install Android Studio or Genymotion:
- Download Android Studio from developer.android.com or Genymotion from genymotion.com (personal edition is free).
- Set up an emulator with Android 12 or 13 for a modern testing environment.
- Pro Tip: Allocate at least 4GB RAM to the emulator to avoid slowdowns.
- Set Up Burp Suite:
- Download the Community Edition from portswigger.net.
- Configure it to listen on a port (e.g., 8080). Set your emulator’s Wi-Fi proxy to your computer’s IP and port to intercept traffic.
- Install MobSF:
- Clone from github.com/MobSF/Mobile-Security-Framework-MobSF.
- Run locally and upload an APK or IPA to get a detailed vulnerability report.
- Practice with test apps like InsecureBank (Android) or Damn Vulnerable iOS App (DVIA).
- Practice Safely:
- Use vulnerable test apps or platforms like TryHackMe for legal practice.
- Keep a testing log to track your findings and experiments.
Common Vulnerabilities to Hunt
Apps can have weaknesses that hackers love to exploit. As a beginner, focus on these common issues found in .apk and .ipa files:
- Insecure Data Storage: Apps may store sensitive data, like passwords or API keys, in plaintext. Check files like preferences or databases during static analysis with MobSF or APKTool.
- Weak Authentication: Some apps have flimsy login systems, allowing bypasses. Use Frida to test if you can skip authentication checks.
- Insecure Communication: Apps may send data over unencrypted HTTP instead of HTTPS, exposing it to interception. Burp Suite helps spot this.
- Improper Permissions: Android APKs might request unnecessary permissions (e.g., accessing your camera for a notepad app). Inspect the AndroidManifest.xml with APKTool.
- Hardcoded Secrets: Developers sometimes embed API keys or credentials in the code. Decompile APKs or IPAs to find these.
Basic Testing Techniques
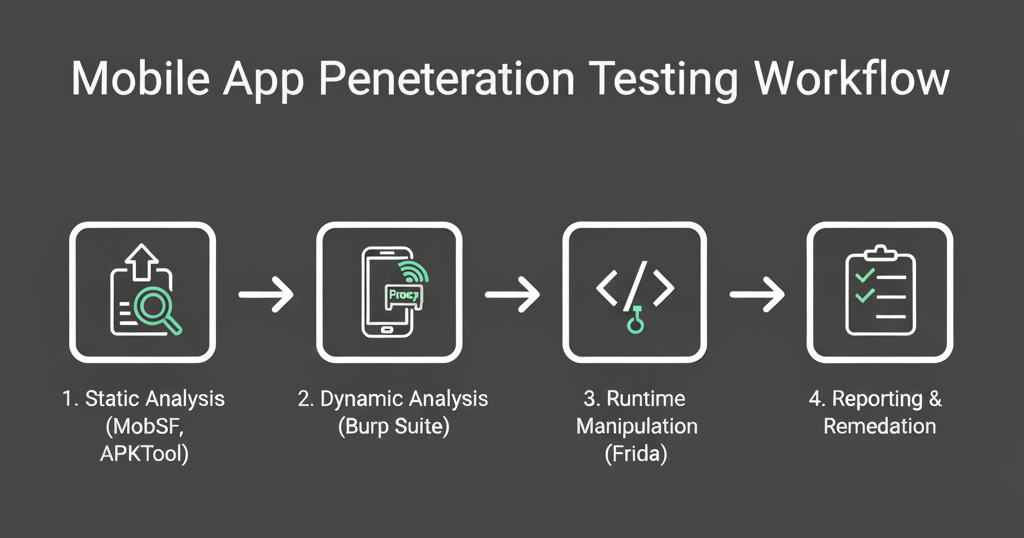
Now that your lab is ready, try these beginner-friendly techniques to start finding vulnerabilities:
Static Analysis with MobSF:
- Upload an APK or IPA to MobSF. It scans for issues like insecure storage or hardcoded secrets and generates a report.
- Look for high-severity findings, such as plaintext credentials, and note them in your testing log.
Decompiling with APKTool:
- Use APKTool to decompile an Android APK (apktool d app.apk). Check the AndroidManifest.xml for excessive permissions or inspect code for hardcoded keys.
- For iOS, use otool on an IPA (requires a Mac) to analyze binaries, but stick to APKs for now as they’re easier.
Dynamic Analysis with Burp Suite:
- Run your app in an emulator (like Genymotion) and route its traffic through Burp Suite.
- Check for unencrypted HTTP requests or sensitive data (e.g., passwords) sent in cleartext.
Hooking with Frida:
- Install Frida and use it to hook into an app’s processes (e.g., frida -U -f com.example.app).
- Test if you can bypass a login by modifying function outputs, like authentication checks. Start with test apps like InsecureBank.
Practice on Test Apps:
- Download InsecureBank (Android) or Damn Vulnerable iOS App (DVIA) to practice safely. These apps are designed with intentional flaws for learning.
Good Luck Cracking Those Apps!
You’re now equipped to start hunting vulnerabilities like a pro! Each app is a new case for your cyber detective skills—dig into those APKs, intercept that traffic, and keep the mobile world secure. Stay ethical, practice regularly, and drop a comment if you’re stuck or want to share your first bug find. Here’s to cracking apps and brewing strong coffee—may your tests be smooth and your exploits legendary!