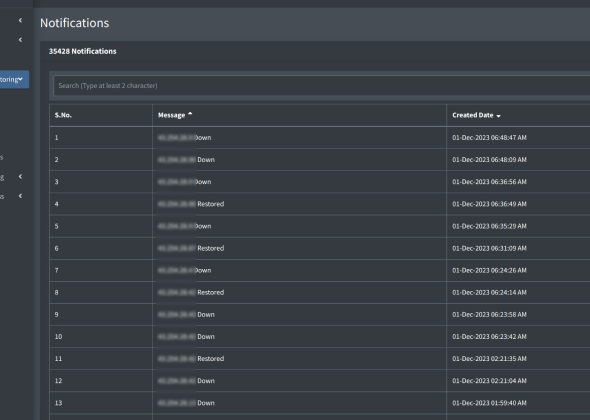
Uptime & Latency Monitoring
Continuous scrutiny of your digital gateways, ensuring they remain impregnable.
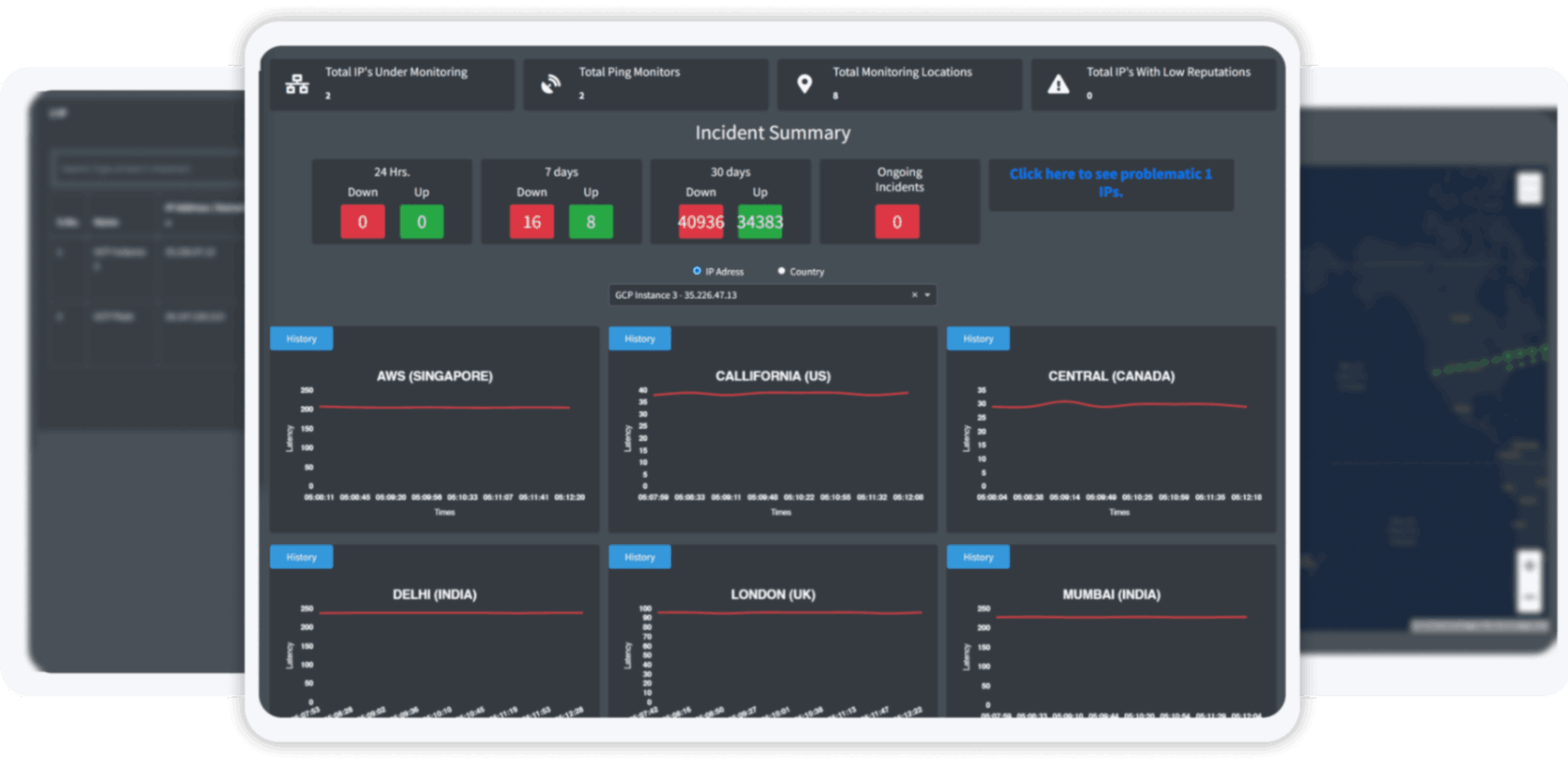

Continuous scrutiny of your digital gateways, ensuring they remain impregnable.

Continuous scrutiny of your digital gateways, ensuring they remain impregnable.
Set traps, lure threats, and monitor with our avant-garde honeypot services.
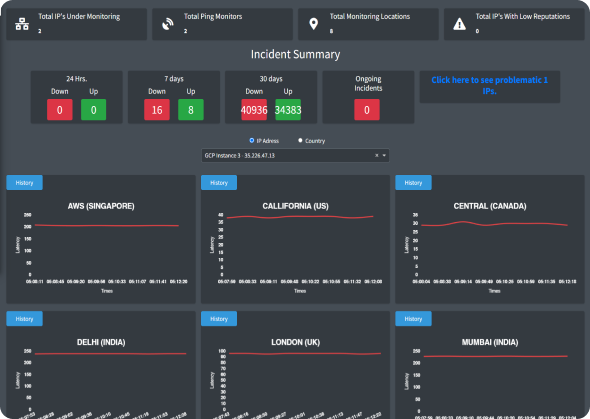
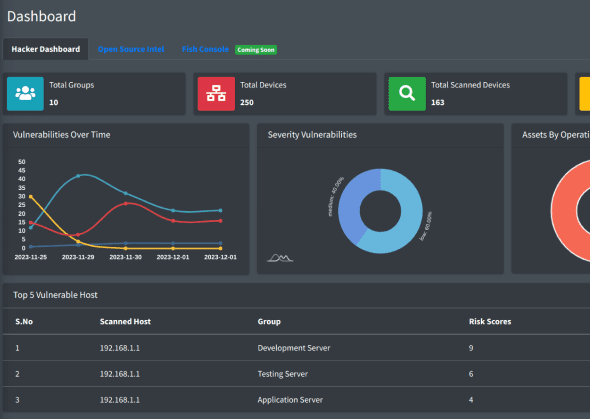
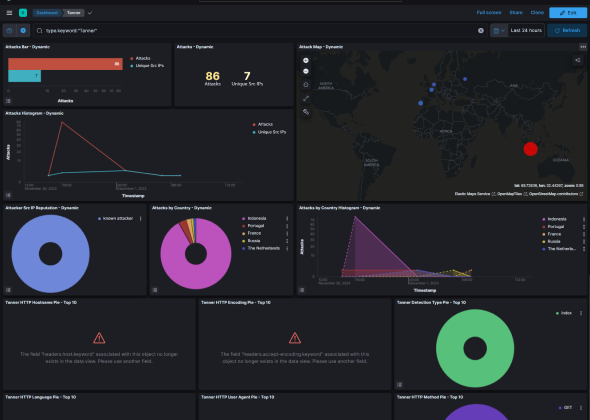
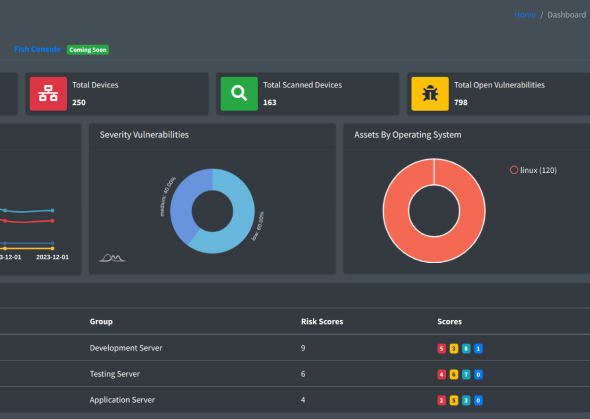
Cloud-based Vulnerability Management System
Start by signing up for our cloud-based Vulnerability Management System. Our platform is designed to help you identify and address system vulnerabilities effectively.
