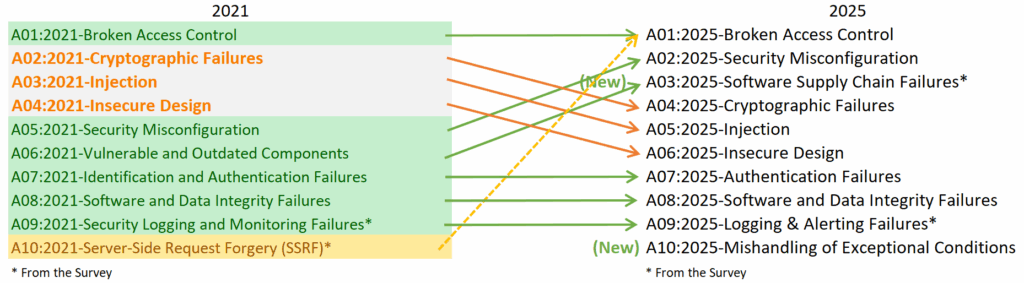
Every few years, the Open Web Application Security Project (OWASP) updates its flagship Top 10 list, a critical resource that defines the most significant security risks facing web applications. The 2025 list is more than just a re-ranking; it’s a clear signal that the attack surface is evolving.
First, a quick glance at the evolution:
A Deep Dive into Each of the OWASP Top 10: 2025
Let’s dissect each point, providing context, real-world relevance, and actionable advice.
A01: Broken Access Control
What it is: When users can access data or functions they shouldn’t be authorized to see or perform. This isn’t just about admin panels; it’s about any unauthorized interaction.
Real-world Example: Imagine being able to change a single digit in a URL (/users/profile?id=123 to /users/profile?id=124) and suddenly viewing another user’s private profile, complete with personal data. This is Insecure Direct Object Reference (IDOR), a prime example of broken access control. Or perhaps a regular user accessing an admin-only feature by simply knowing its endpoint.
Why it matters: It consistently leads to data breaches, unauthorized modifications, and complete system compromise. It’s often simple to exploit and devastating in impact.
A02: Security Misconfiguration
What it is: Incorrectly configured security settings in any part of the application stack – from the operating system and web server to databases, frameworks, and especially cloud services.
Real-world Example: Leaving default credentials enabled on a database, an S3 bucket configured for public read/write access, an ElasticSearch instance exposed to the internet, or unnecessary services running on a server. Remember that major Capital One breach? It was partly due to a misconfigured web application firewall (WAF) rule.
Why it matters: With the rise of cloud computing and complex microservice architectures, configuration errors are rampant and often have a wider blast radius.
A03: Software Supply Chain Failures
What it is: This is the evolution of “Vulnerable and Outdated Components.” It encompasses risks throughout the entire software supply chain: vulnerable third-party libraries, open-source packages, malicious code injected during the build process, compromised CI/CD pipelines, or even upstream dependencies.
Real-world Example: The Log4Shell vulnerability (Log4j) perfectly illustrates this. A ubiquitous logging library, deeply embedded in countless applications, suddenly had a critical remote code execution flaw. The attack wasn’t on the application directly, but on one of its foundational components. Or consider the SolarWinds attack, where attackers compromised the build system to inject malicious code into legitimate software updates.
Why it matters: Modern applications are mosaics of components. A single weak link in this chain can compromise the entire application, even if your custom code is perfectly secure.
A04: Cryptographic Failures
What it is: Flaws related to cryptography, such as using weak algorithms, insufficient key management, or failing to encrypt sensitive data at rest or in transit. This leads to exposure of sensitive data.
Real-world Example: An e-commerce site storing credit card numbers in a plaintext database, or using weak hashing algorithms like MD5 for passwords. Or transmitting user data over HTTP instead of HTTPS, allowing network sniffers to capture sensitive information.
Why it matters: Data is king, and cryptographic failures make it vulnerable to theft, modification, and exposure, leading to regulatory fines and reputational damage.
A05: Injection
What it is: When untrusted data is sent to an interpreter as part of a command or query, tricking the interpreter into executing unintended commands or accessing unauthorized data.
Real-world Example: SQL Injection (' OR '1'='1) is the poster child, allowing attackers to bypass authentication or dump entire databases. Cross-Site Scripting (XSS) where malicious scripts are injected into web pages viewed by other users. Command Injection where attackers run arbitrary system commands.
Why it matters: Despite being a well-known vulnerability, injection attacks remain prevalent due to insufficient input validation and output encoding.
A06: Insecure Design
What it is: A new category in 2021, it highlights security flaws that arise from design and architectural decisions, rather than implementation bugs. It’s about fundamental weaknesses in how an application is conceived.
Real-world Example: An application designed without proper segregation of duties between user roles, leading to easy privilege escalation. Or a payment gateway implemented without adequate rate limiting, making it vulnerable to brute-force attacks on card numbers. A REST API that doesn’t enforce field-level access control at the design stage, allowing users to inadvertently update fields they shouldn’t.
Why it matters: Design flaws are often harder and more expensive to fix later in the development cycle. They represent a fundamental misunderstanding of security principles.
A07: Authentication Failures
What it is: Flaws in how user identities are verified, credentials stored, and session management implemented. It used to be “Identification & Authentication Failures.”
Real-world Example: Weak password policies (e.g., allowing “password123”), missing Multi-Factor Authentication (MFA), easily guessable session IDs, or not expiring sessions after inactivity. A common attack is brute-forcing login attempts due to a lack of rate limiting.
Why it matters: Compromised authentication leads directly to unauthorized account access, data theft, and complete impersonation.
A08: Software or Data Integrity Failures
What it is: This category focuses on risks related to assuming the integrity of software updates, critical data, or CI/CD pipelines without proper verification. It also includes cases where applications rely on client-side data without server-side validation.
Real-world Example: A banking application that allows a user to modify their account balance value in a client-side JavaScript variable, and the server blindly trusts this input without re-validating the transaction logic. Or a system that downloads software updates without verifying cryptographic signatures, making it vulnerable to malicious updates. Deserialization of untrusted data leading to remote code execution (e.g., Java deserialization vulnerabilities).
Why it matters: Lack of integrity checks can lead to unauthorized data manipulation, arbitrary code execution, and system compromise.
A09: Logging & Alerting Failures
What it is: Insufficient logging, monitoring, and alerting. Without proper logs and timely alerts, security incidents go unnoticed, allowing attackers to persist and cause more damage.
Real-world Example: An attacker breaches a system, but because there’s no logging of failed login attempts or unusual activity, they can operate undetected for months, exfiltrating sensitive data. Or, critical security events are logged but not aggregated, analyzed, or generate alerts for security teams. The Equifax breach was famously characterized by a long period of undetected intrusion.
Why it matters: You can’t protect what you can’t see. Poor logging and alerting make it impossible to detect, investigate, and respond to security incidents effectively.
A10: Mishandling of Exceptional Conditions
What it is: This brand-new category addresses security vulnerabilities that arise when an application encounters unexpected errors, exceptions, or logical failures. It focuses on unsafe behavior during these “exceptional conditions.”
Real-world Example:
- Data Leakage: An application crashes and displays a full stack trace to the user, revealing internal file paths, database queries, and server details that an attacker can use for further exploitation.
- Failing Open: A critical security component (like an authentication service) fails due to an exception, and instead of denying access, the application grants access by default (“failing open”) to avoid disruption, creating a bypass.
- Resource Exhaustion: An unhandled exception in a loop or resource allocation could lead to a denial-of-service (DoS) if not gracefully handled, consuming all available memory or CPU.
Why it matters: Attackers often provoke errors to gain information or bypass controls. How an application fails is just as important as how it succeeds securely.
The Takeaway: Shift Left, Shift Right, Secure Everywhere
The OWASP Top 10: 2025 isn’t just a list; it’s a strategic roadmap. It tells us that:
- Design Matters More Than Ever: With “Insecure Design” firmly in place and the emphasis on “Mishandling of Exceptional Conditions,” security must be baked in from the very first whiteboard session, not bolted on at the end. Threat modeling is no longer optional.
- The Supply Chain is Your New Perimeter: “Software Supply Chain Failures” is the biggest new warning. Your application is only as strong as its weakest link, and those links are often outside your direct control.
- Operational Security is Critical: “Logging & Alerting Failures” and “Security Misconfiguration” rising in rank show that how you deploy and monitor your applications is just as vital as the code itself.
- The Classics Endure: “Broken Access Control” and “Injection” still top the charts, proving that fundamental security practices remain essential.
This isn’t about fear; it’s about empowerment. By understanding these risks, developers, architects, and security teams can build more resilient, trustworthy, and secure applications.
~Abhishek Anjana

















