A vulnerability-detection tool for penetration testing — we’ll focus on Wireshark and how it can reveal login data sent over unencrypted HTTP and FTP. This is important for security pros on both offensive and defensive teams, so let’s keep it focused and responsible.
First, a quick refresher: HTTP is how web pages and web forms are exchanged, and FTP is an older protocol used to upload and download files. Both can send credentials in plain text if not secured, which is why attackers often target them.
Wireshark can capture traffic at the router or switch level and lets you inspect packets with powerful filters to uncover these weaknesses. This guide is meant for penetration testing tools and workflows used by red teams and blue teams — only run captures in a controlled lab (your own sandbox VMs) or on systems where you have explicit permission.
Launch Wireshark in Kali Linux
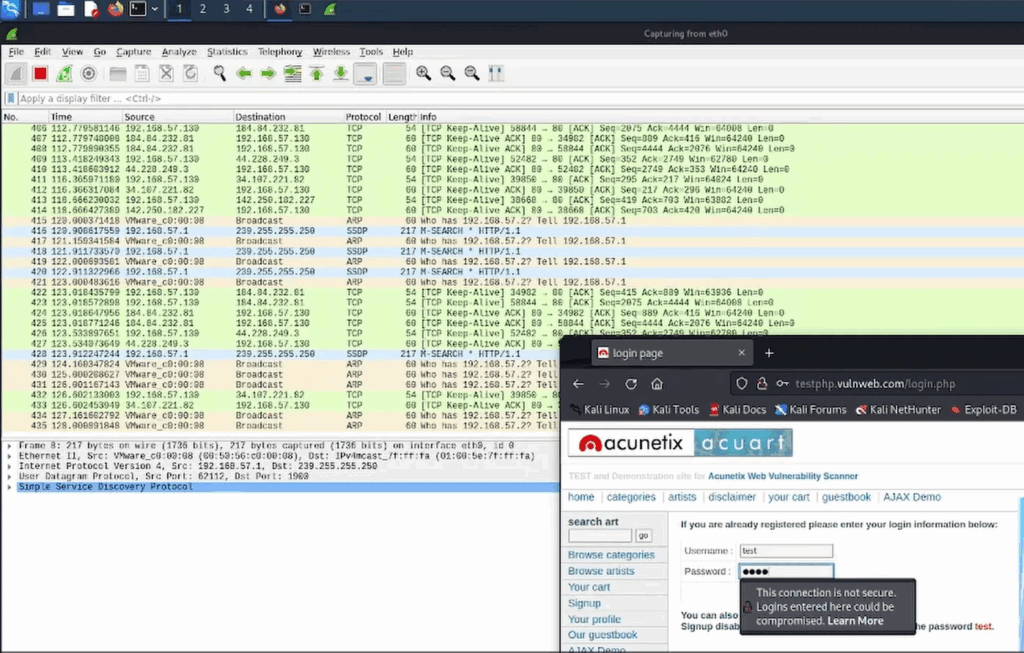
Now, let’s start Wireshark and start capturing packets information. Select the network interface and begin packet capture. Test as website using HTTP and then an FTP server, Wireshark starts capturing the packets exchanged during these login processes. Filter the captured packets to specifically extract HTTP login credentials.
Using Wireshark’s filtering tools, narrow the view to show only HTTP traffic so you can observe the authentication exchange during a test login. In a controlled, permitted environment, perform an HTTP login while the capture runs and watch how the application-level packets are presented.
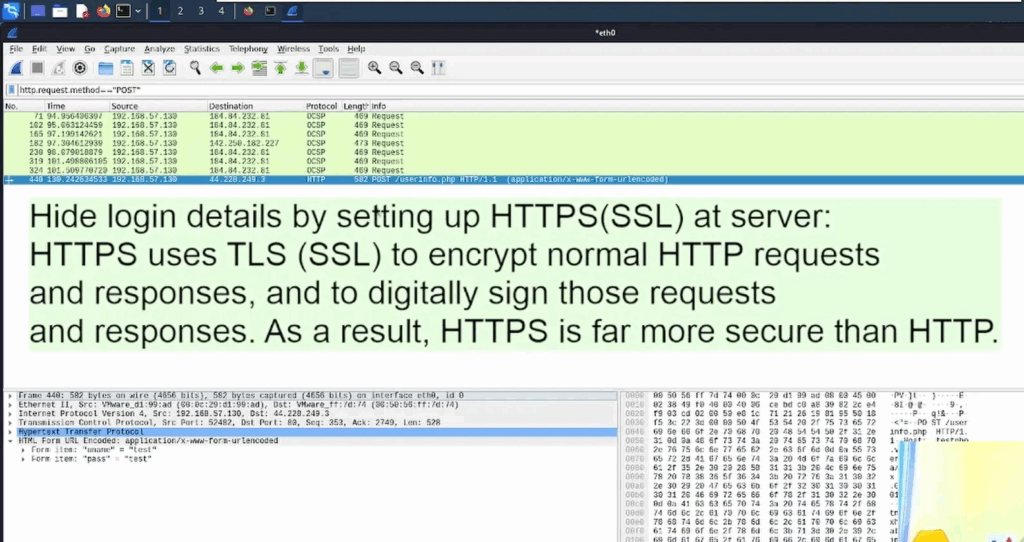
Next, do the same for FTP: apply a filter that isolates FTP traffic and run an FTP login on your lab server. Wireshark will show the sequence of packets involved in authentication — use this to confirm whether credentials are being sent securely or in cleartext, and to document any insecure behavior for remediation.
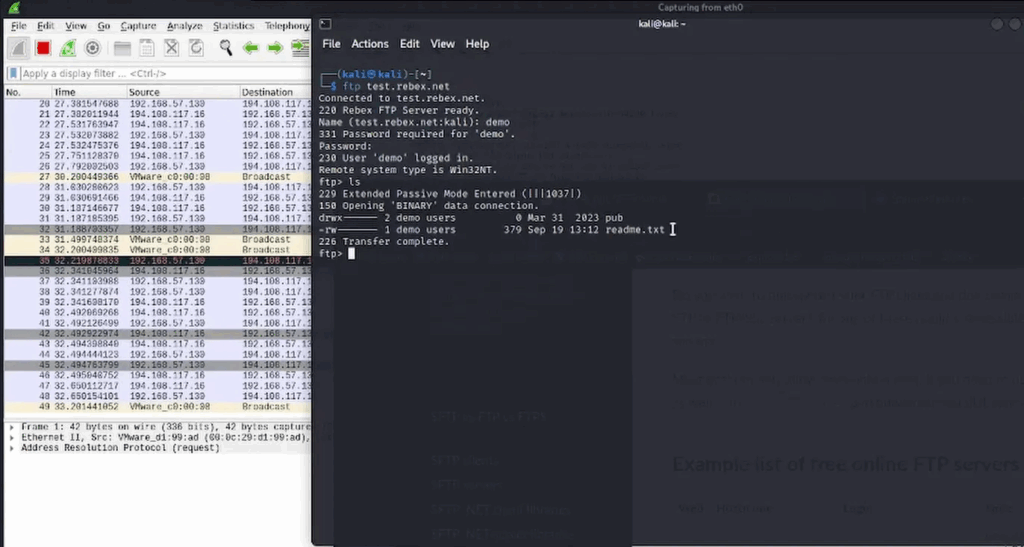
Use a sandboxed FTP server for penetration testing so Wireshark can safely capture and inspect the traffic. Make sure this is done in an isolated lab or on systems you have explicit permission to test.
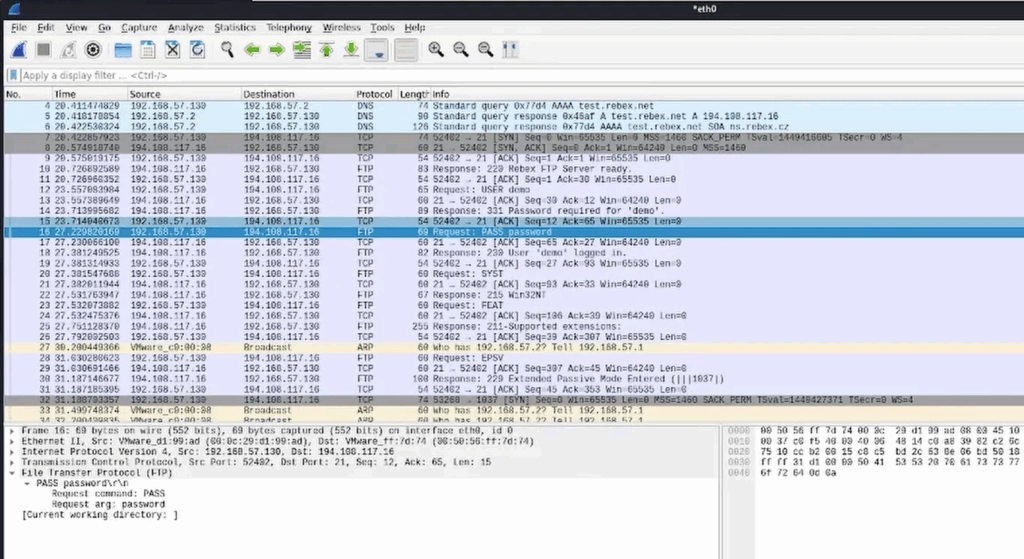
Now that we’ve captured authentication-related packets in a controlled test environment, let’s analyze the results. Inspect the packet traces to confirm whether login exchanges are sent in plaintext or protected by encryption — look for signs of insecure authentication rather than trying to harvest actual usernames or passwords. This kind of analysis highlights why encoding, server-side encryption, and secure protocols matter to protect sensitive data in transit. (Note: Wireshark can also be used to investigate TLS/HTTPS behavior and certificate chains — that’s a deeper topic for another time.)Keep in mind these weaknesses make connections vulnerable to man-in-the-middle attacks on untrusted networks like public Wi‑Fi in cafés and airports, so always use secure channels when possible.If this helped, please like or comment. Thanks for reading — stay safe and test only in authorized environments.
~Amber Sharma

















