Fuzz Testing, often called fuzzing, is a powerful software testing technique used to uncover hidden bugs and security flaws in computer programs, operating systems, and network protocols.
In simple terms, fuzzing means sending random or unexpected data (called fuzzed inputs) to a program and observing how it reacts.
If the program crashes, hangs, or behaves strangely — that’s a sign something might be wrong or vulnerable.
The main goal of fuzz testing is to find:
- Security vulnerabilities
- Software crashes
- Unexpected or unstable behavior
- Logic flaws or input-handling weaknesses
Types of Fuzz Testing
Here are the most common types of fuzzing used in cybersecurity and software testing:
1. API Fuzzing
Targets APIs (Application Programming Interfaces) to find flaws or weak points in the communication between applications.
2. Input Fuzzing
Focuses on modifying user inputs such as command-line arguments, file uploads, or form data to check how the program handles them.
3. File Format Fuzzing
Tests software that reads or processes files (like PDFs, images, or Word docs) by giving it slightly corrupted or malformed files.
4. Mutation Fuzzing
Takes valid inputs and mutates them (flips bits, deletes characters, adds random data) to test the system’s robustness.
5. Protocol Fuzzing
Used for network-based applications — it sends malformed or invalid packets to test how the system handles unexpected communication.
6. Generation Fuzzing
Generates entirely new inputs from scratch, based on known data formats or rules.
7. Web Fuzzing
Targets web applications by sending invalid or random HTTP requests, parameters, and forms to uncover potential vulnerabilities.
8. Differential Fuzzing
Compares two similar programs or systems to find differences in how they handle the same input.
9. Smart Fuzzing
Uses intelligent algorithms or machine learning to prioritize and guide the fuzzing process, making it faster and more effective.
10. Grammar-Based Fuzzing
Uses predefined grammar rules to generate structured test data, ensuring both valid and invalid cases are tested.
How Does Fuzz Testing Work?
Fuzz testing typically follows a simple, step-by-step process:
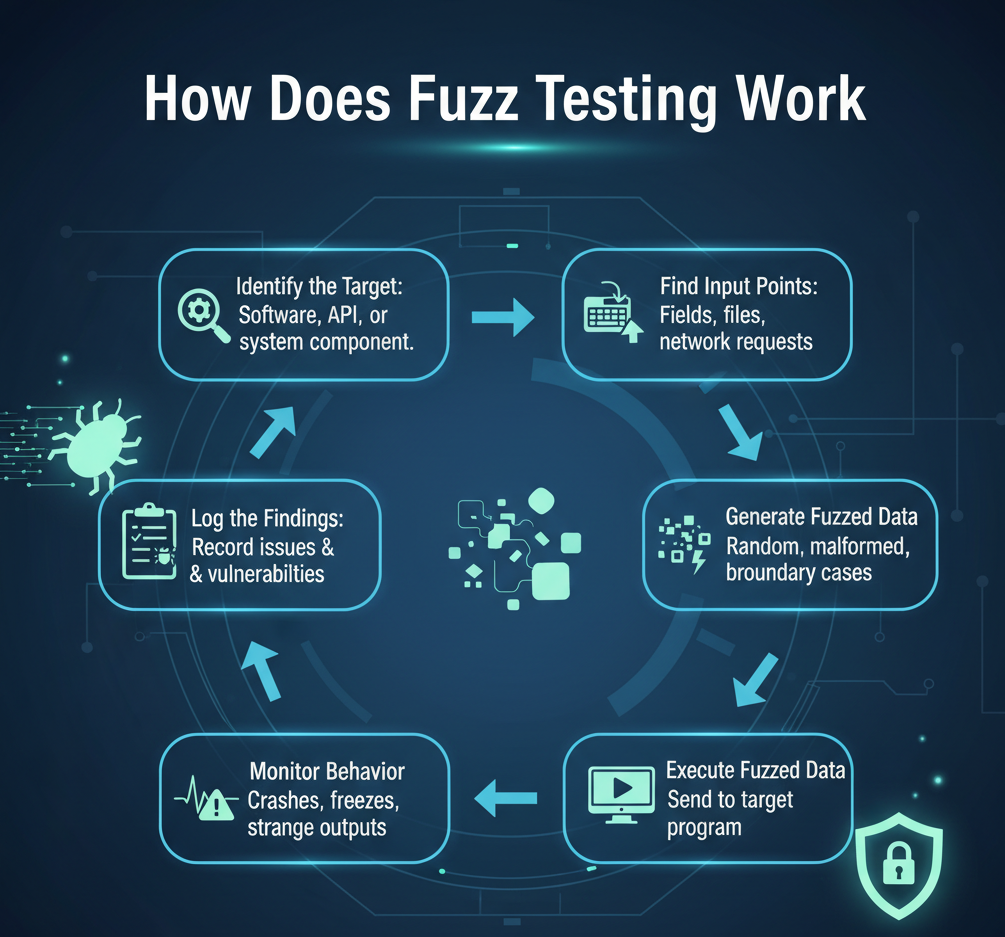
- Identify the Target:
Choose the software or system component you want to test (e.g., an API, login form, or file parser). - Find Input Points:
Identify where the program accepts data — such as input fields, files, or network requests. - Generate Fuzzed Data:
Create different types of test data — random, malformed, or boundary cases. - Execute Fuzzed Data:
Send this data to the target program and see how it responds. - Monitor Behavior:
Observe for signs of crashes, freezes, or strange outputs. - Log the Findings:
Record any issues or vulnerabilities discovered for developers or security teams to fix.
Why is Fuzz Testing Important?

It helps uncover hidden bugs before attackers can exploit them.
It improves software reliability and security.
It can reveal zero-day vulnerabilities that traditional testing might miss.
It’s an essential part of penetration testing and vulnerability assessment.
Final Thoughts
Fuzz testing might sound complex, but it’s one of the most effective ways to find unknown bugs and strengthen software security.
If you’re a pentester or cybersecurity learner, mastering fuzzing will take your vulnerability research to the next level.
~By Abhishek Anjana

















