Welcome back, hacker.
In Part 1, we built our foundation and assembled our arsenal. Now, the theory ends. It’s time to declare war on that .exe file.
Most beginner guides give you five complicated ways to proxy traffic. They leave you confused and frustrated when nothing works. Forget that.
This guide will teach you the one method to rule them all for intercepting thick client traffic. The method that works when others fail. The method that cracks open custom protocols, FTP, and raw TCP streams.
We will use mitm_relay, the ultimate weapon for forcing any client’s traffic through Burp Suite.
Let’s begin.
Phase 1: Deep Recon with Process Monitor (ProcMon)
Before we intercept, we need a target. We need to know where the client is trying to go. This is where Process Monitor (ProcMon) becomes your most important tool.
Your Goal: To find the server’s IP address and port number.
Step-by-Step ProcMon Recon
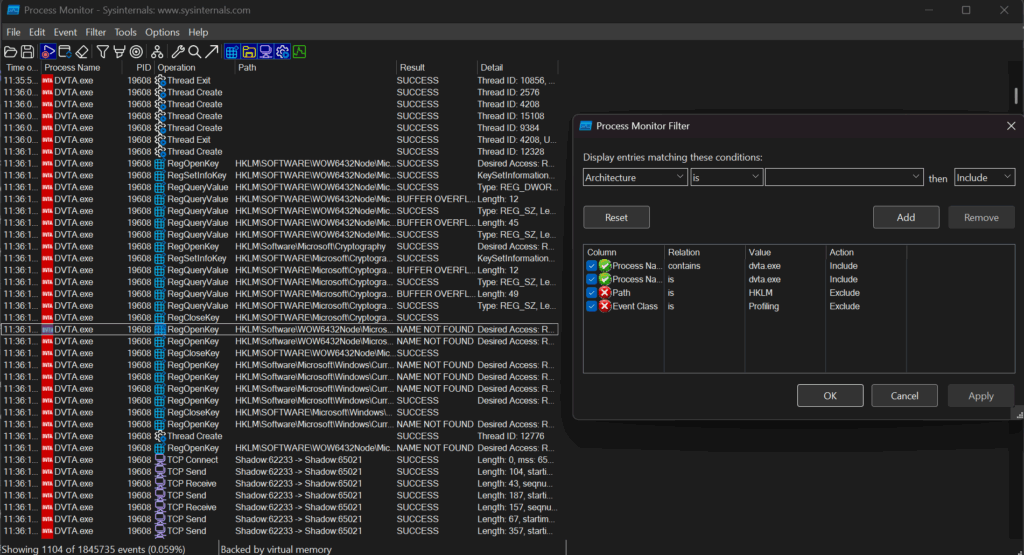
- Launch ProcMon. You’ll be greeted by an overwhelming torrent of data. We need to filter this.
Caption: The default ProcMon view is a firehose of information. We need to focus it.
- Set a Filter for Your Target.
- Click Filter -> Filter….
- Create a new filter where Process Name is [YourApp].exe (e.g., filezilla.exe).
- Click Add and then OK.
- Boom. Now the log only shows operations from your target application.
- Hunt for the Connection.
- Let the application start and try to connect.
- In ProcMon, look for TCP Connect events in the Event Class column.
- This is gold. The Path column will show you the exact IP:Port the client is trying to connect to (e.g., 10.10.0.73:21111). Write this down.
Phase 2: The One Method to Rule Them All: mitm_relay
Forget Proxifier. Forget invisible proxying. For custom protocols (FTP, TCP, UDP), mitm_relay is the most powerful and reliable tool. It creates a transparent proxy, perfect for manipulating any traffic.
Your Goal: To place yourself directly between the client and the server.
Prerequisite: Disable Anti-Spoofing on the Server
Many servers have protections against IP spoofing. We must disable this for our attack to work.
Example: FileZilla Server
- On the server machine, open the FileZilla Server Interface.
- Go to Edit > Settings.
- Navigate to General settings > FTP over TLS settings.
- Find and disable “IP checks”. This setting blocks man-in-the-middle attacks.
- Click OK.
Step-by-Step: Launching the Attack
Step 1: Install the Weapon
Open a command prompt on your attacker machine (where Burp is running) and install the tool:
Command: pip install mitm_relay
Step 2: Run the Relay Command
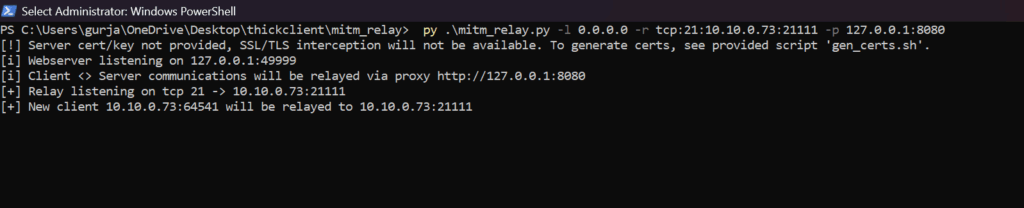
Using the IP and port you found from ProcMon, run this command:
Command: mitm_relay -l 0.0.0.0 -r tcp:21:10.10.0.73:21111 -p 127.0.0.1:8080
Command Breakdown:
- -l 0.0.0.0: Listen on all interfaces on your machine.
- -r tcp:21:10.10.0.73:21111: The routing rule. “Take any TCP traffic sent to my port 21 and forward it to the real server at 10.10.0.73:21111.”
- -p 127.0.0.1:8080: The proxy rule. “But first, send ALL that traffic through Burp Suite at this address.”
In simple terms, this sets up the chain:
Thick Client -> Your Machine -> Burp Suite -> Real Server
Step 3: Redirect the Client
Now, trick the client into connecting to YOU instead of the real server.
Edit your hosts file (C:\Windows\System32\drivers\etc\hosts as Administrator). If the client connects to a domain like ftp.mycompany.com, add this line:
[YOUR-ATTACKER-IP] ftp.mycompany.com
If the client uses a hardcoded IP, change the IP in the client’s config file to your attacker IP.
Step 4: Configure Burp Suite
- Ensure Burp’s proxy listener is active on 127.0.0.1:8080.
- No special configuration is needed. The relay does all the work.
Phase 3: First Blood – Let’s Hack!
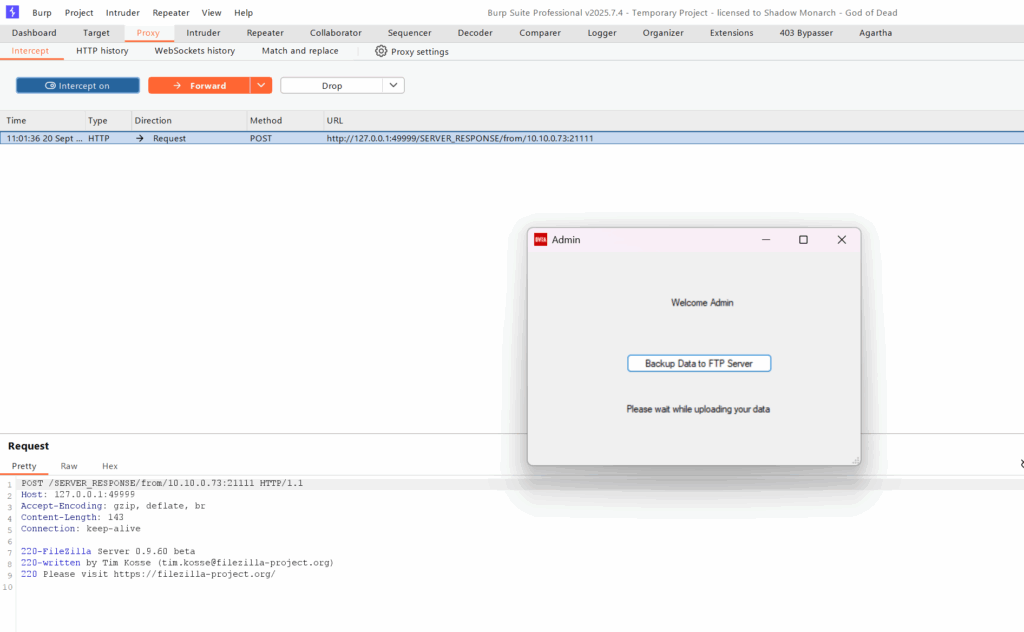
With the relay running, launch your thick client. Watch the magic happen.
- Traffic will flow into Burp. Check the HTTP History tab. Even though it’s FTP/TCP traffic, it will appear there in its raw form.
- Look for plaintext credentials. FTP and many custom protocols send usernames and passwords in clear text. This is a very common finding.
- Replay and Manipulate. You can right-click any request and send it to Repeater. Now you can manipulate the raw TCP streams and fuzz for vulnerabilities.
The Beginner’s Journey: Complete
You’ve done it. You’ve mastered the single most important skill in thick client pentesting.
Remember your path:
- You gathered intelligence (ProcMon Recon).
- You deployed your ultimate weapon (mitm_relay).
- You breached the perimeter (Redirected the client).
- You began your assault (Found plaintext credentials in the stream).
You now have the fundamental skills to approach almost any thick client, find its weak spots, and intercept its secrets. This is the core of the craft.
From here, your path is to practice this relentlessly. Then, you will be ready to dive into the advanced world of reverse engineering and memory manipulation.
Now go forth and break things (ethically).

















