Welcome, future hackers. You can fuzz endpoints, find SQLi in your sleep, and bypass authentication on web apps blindfolded. But now you’ve been handed a .exe file. You point Burp at it. Nothing happens. It’s a black box. It’s intimidating.
Take a deep breath. This is where the fun begins.
Welcome to the Beginner’s Series on Thick Client Pentesting. This isn’t just about finding bugs; it’s about learning to own an entire application ecosystem, from the binary on the desktop to the database on the server.
We’ll transform you from someone who dreads that .exe file into someone who can’t wait to tear it apart. Let’s build your foundation.
What Exactly Are We Hacking? It’s All About Architecture
Forget browsers for a minute. To understand thick clients, you need to understand how they’re built. They typically follow one of two architectural models:
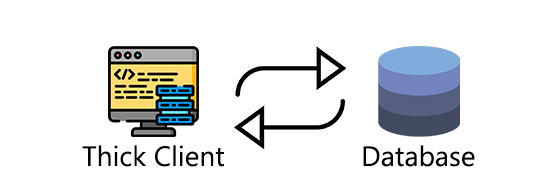
1. Two-Tier Architecture (The Direct Line)
Imagine a application that talks directly to a database on the network. This is a Two-Tier architecture.
- Tier 1 (Client): The application on your machine. It contains the user interface and most of the business logic.
- Tier 2 (Server): The backend database server (e.g., MySQL, MSSQL).
- The Connection: Direct and often persistent. The client application might have the database credentials hardcoded or stored in a config file.
- Why it matters for pentesters: A direct database connection is a goldmine. Find the credentials, and you own the entire database.
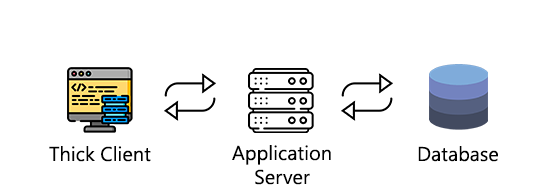
2. Three-Tier Architecture (The Modern Standard)
Most modern apps use a Three-Tier architecture, which adds a crucial middle layer.
- Tier 1 (Presentation Tier): The application on your machine. It’s only responsible for the user interface.
- Tier 2 (Application/Logic Tier): A middle-tier server that contains the core application logic. This is usually a set of APIs (REST, SOAP, gRPC).
- Tier 3 (Data Tier): The backend database.
- The Connection: The client (Tier 1) only talks to the API server (Tier 2), which then talks to the database (Tier 3). The client never directly accesses the database.
- Why it matters for pentesters: Your main point of attack shifts to the APIs between the client and the middle tier. You’ll be hunting for insecure API endpoints, broken authentication, and parameter manipulation.
Thick Client vs. Web App: A SWAT Team vs. a Sniper
This is the mindset shift. Don’t think of this as “another app test.” Think of it as a different kind of warfare.
| Aspect | Web App Testing (The Sniper) | Thick Client Testing (The SWAT Team) |
| Target | One target: the server. | The entire system: binary, OS, data, and server. |
| Approach | Precise. You take a single shot (a crafted HTTP request) at a specific endpoint. | Overwhelming force. You breach, clear, and secure every component. |
| Traffic | HTTP/S. Easy to proxy and predict. | HTTP/S, custom TCP/UDP, gRPC, WebSockets. A nightmare to proxy. |
| Data & Logic | On the server. You can’t see it, only influence it. | On YOUR machine. You can see it, touch it, reverse it, and manipulate it directly. |
| Tool Focus | Burp Suite, Browser. | Burp Suite + Debuggers + Sysinternals + RE Tools. |
Why this matters: As a thick client pentester, you aren’t just looking for a single flaw. You’re engineering a takeover. You might start by reverse-engineering a password check, then use that password to connect to a database, find an API key, and use that to compromise the backend server. It’s a full-spectrum assault.
Your “To-Hack” List: The Key Attack Vectors
As a beginner, your mission is to systematically check these core areas. This is your checklist for every new client you encounter:
- Insecure Communication: Does it send passwords over plain HTTP? Does it accept any SSL certificate (making MITM attacks trivial)?
- Secrets in the Binary: Are there API keys, credentials, or hidden endpoints just sitting inside the .exe or .dll files?
- Local Data Exposure: Where does it store user data? In a local SQLite database? A config file? The Windows Registry? Is it encrypted? (Spoiler: Often, it’s not.)
- DLL Hijacking: When the app starts, does it look for libraries in places where you could drop a malicious one?
- Memory Manipulation: Can you change values in the application’s memory to alter your balance, bypass a license check, or unlock features?
- API Endpoints: Once you see the traffic, all your classic web skills (SQLi, IDOR, BOLA) come right back into play.
Building Your Arsenal: The Essential Toolkit
Don’t get overwhelmed. You only need a few powerful tools to start. Download and install these now:
- Burp Suite Professional/Community: The undisputed champion. We’ll use it to intercept and manipulate all HTTP(S) traffic.
- Microsoft Sysinternals Suite: This is your superpower. A free pack of utilities from Microsoft that lets you see everything happening on your Windows machine.
- Process Monitor (ProcMon): Your #1 recon tool. It shows you every file, registry key, and network connection the application touches in real-time. This is how you learn what an app is really doing.
- Process Explorer: Like Task Manager on steroids. Perfect for inspecting running processes and their loaded libraries (DLLs).
- dnSpy / ILSpy: The magic wand for .NET applications. This tool can decompile .NET executables back into readable (and even editable) C# code. You can find secrets, understand logic, and patch bugs.
- JD-GUI: The equivalent of dnSpy, but for Java applications (.jar files).
- Strings.exe: A simple command-line tool that pulls all human-readable text out of a binary file. The fastest way to find low-hanging fruit like hardcoded URLs and passwords.
Your Hacking Lab: Practice Safely!
WARNING: Never, ever test an application you do not own or have explicit written permission to test.
You need a safe, legal environment to practice. For thick client pentesting, the go-to vulnerable app is the Damn Vulnerable Thick Client App (DVTA).
- Set up a Virtual Machine: Use VirtualBox or VMware to create a Windows 10 VM. This is your sandbox—where you can break things without consequences.
- Download DVTA: Get it from its GitHub repository: https://github.com/secvulture/dvta
- Install Your Tools: Install all the tools listed above inside your new VM.
What’s Next? Getting Your Hands Dirty.
You now know what to attack and what to attack it with. The theory is over.
It’s time to get practical.
In the next part, we stop talking and start hacking. We’ll dive into deep reconnaissance with ProcMon and learn the essential dark arts of forcing stubborn, non-proxy-aware applications to send their traffic through Burp Suite. This is the critical first step that unlocks everything else.

















